CryptoCurrency Phising Email Analysis
Today a suspicious email was able to get through my hardened spam filter which is rare to me. The key circumstance is that this email is a newly created email that is on my updated resume and it is not linked or signed up to any services at all. You get the idea, this fresh email is for me to know that X person actually physically looked at my resume and contacted me. Unfortunately as we all know the internet is forever and you can’t hide 100%. Let’s get to it shall we.

The bad actors fake name is Bessie Manring and the email in question is ziwezilo@gmail. Let’s get to work on the malicious PDF file named Elon Musk Register OUr. First We’re going to save the email and open it in a sandboxed environment. I’m using one of my Kali Linux machines running in virtualbox that is segmented via vlan.
The PDF is now on my VMs desktop and I renamed it to something shorter to save myself the hassle of typing out the original pdf name during triage. I can just use the history feature once the file name is typed in but I like to type, helps keep my twitter fingers stay ready. I use PDFiD which is a quick way to scan a PDF file for embedded javascript, see Object streams, and more details about the PDF while not having to execute the PDF file.
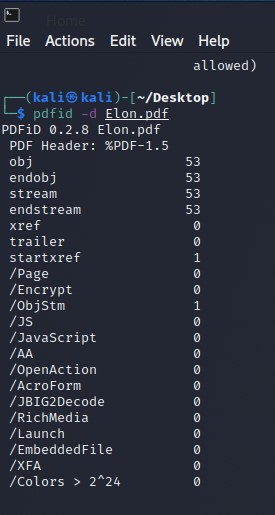
At a quick glance there is nothing that stands out during the scan except that 1 Object Stream. I was more so looking for obfuscation or the scan to pull up some /AA hits which would be automatic actions to execute if the PDF was opened. Let’s be safe and Disarm the PDF with the -d command for practice.
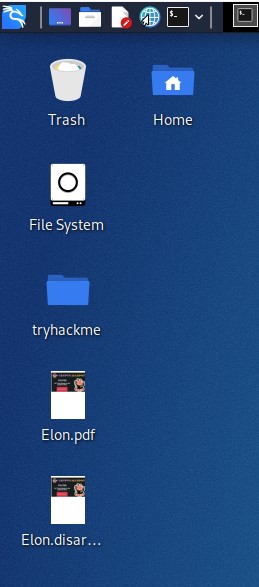
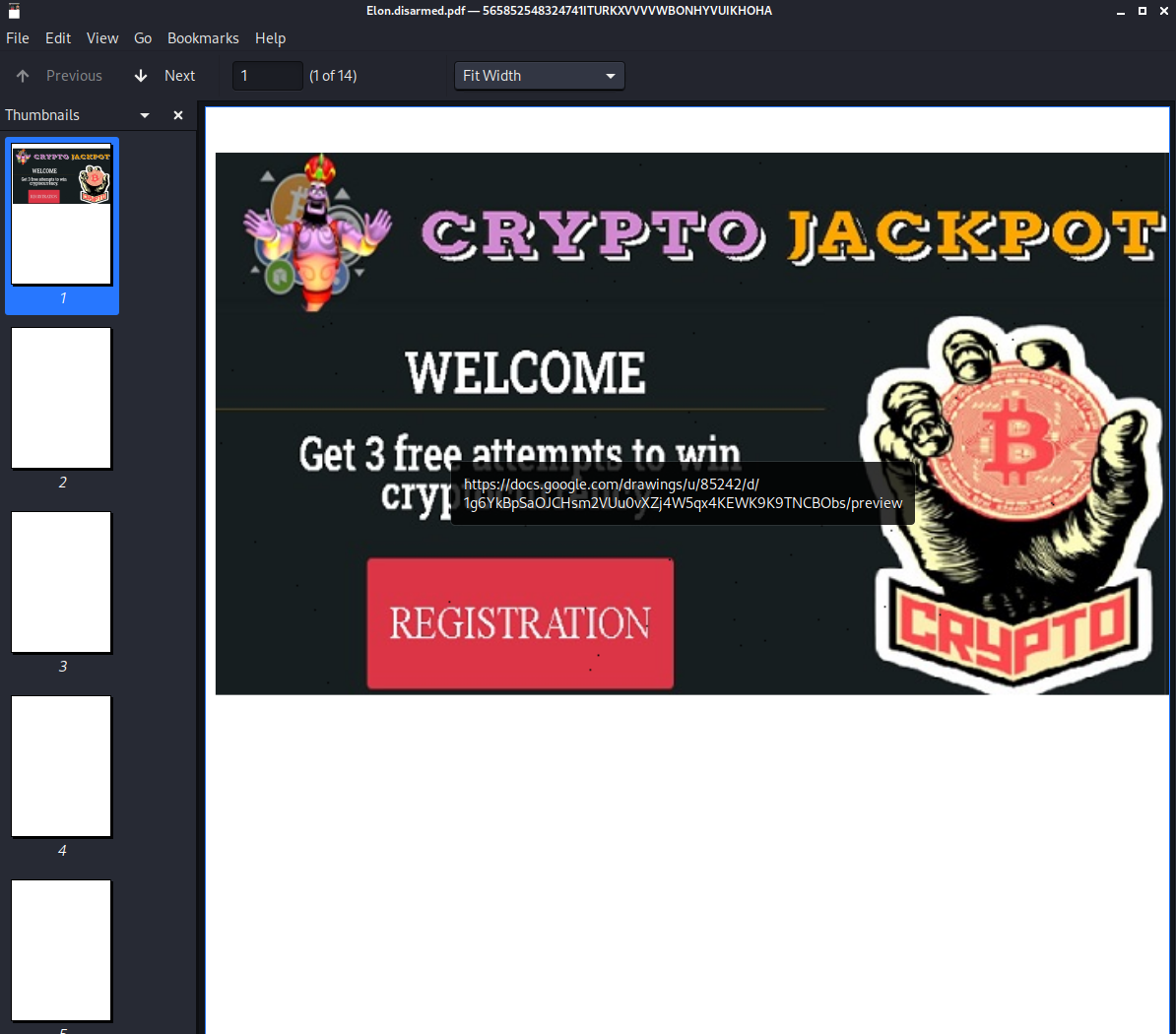
Now that we have a disarmed PDF file let’s open it and see what goodies are inside. It appears at open we get spam banner that links to to a “registration” page. I sure trust that google docs link that is suppose to be a crypto currency jackpot website. Dang it, I wanted it to be a phising email so we can dig deep.
I quote registration page because upon opening the link in a safe manner, it’s a google docs link as shown below. Nothing to see here, just a basic spam email that somehow hit my new email I made.

Unfortunately what we thought was a malicious phising/malware email is turning more into a spam email. These emails are fairly common and this email links to your typical cryptocurrency online gambling website. You’ll load onto the page, type in any fake name and email so you can get some spins. In this case you spin a few times for a chance to win some bitcoin or other cryptocurrency.
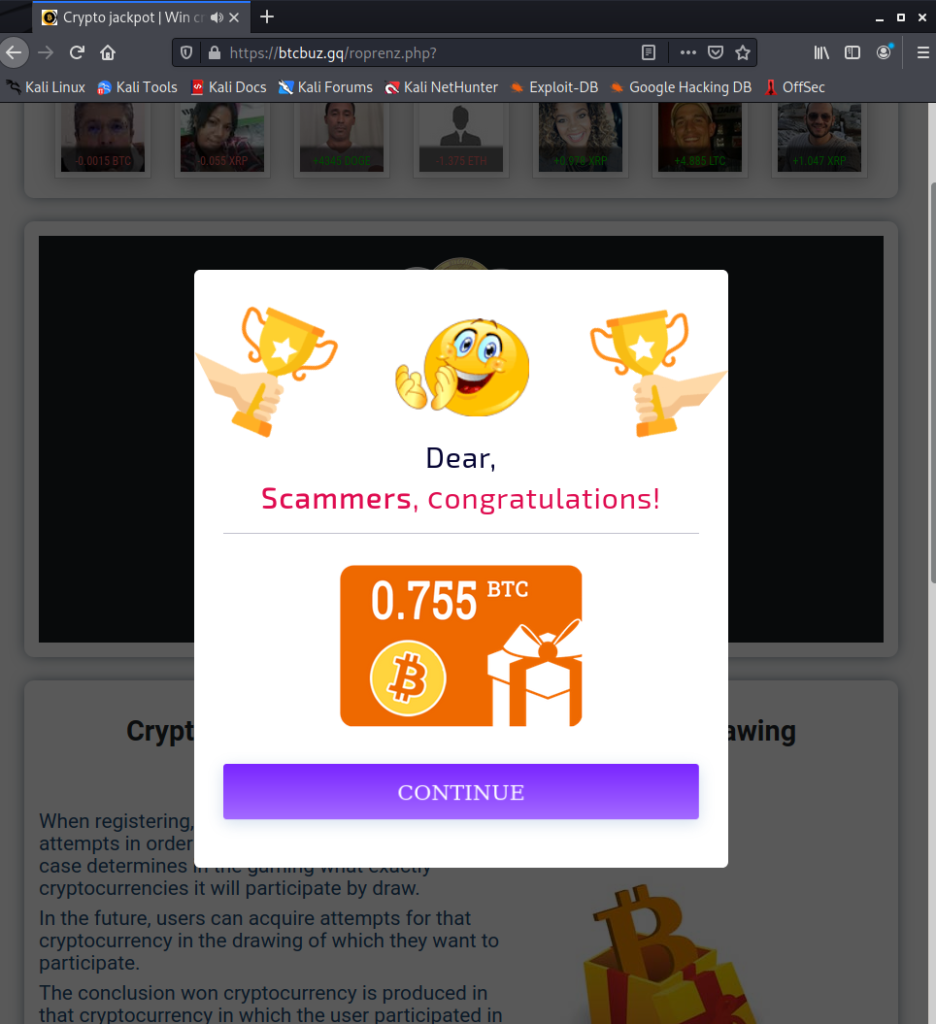
Now for me to claim my free 34,000 USD I have to pay a commission to the bitcoin miners equal to 0.0015 BTC = to $67 USD as of 3/31 to their auto generated wallet address.
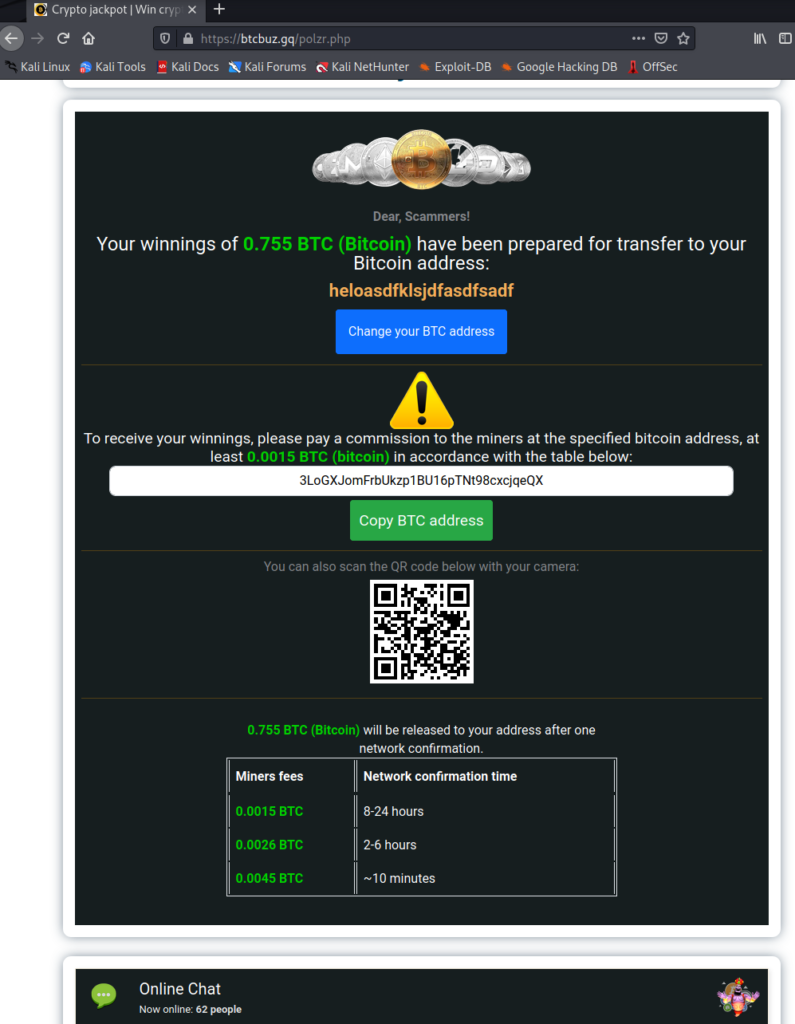
Upon further review and a traffic analysis… I’m throwing out the red flag, challenging this as a basic spam email that originates from Russia. I’ll take the ball on the right hash at the 10 yard line please.