I Created A Honeypot Using Windows 10 Remote Desktop, Then Russians Attacked Me
Do you want to know how dangerous it is to set up your home computers to allow remote logins? Maybe you followed one of those tech Youtube videos that headlines with “How To Setup Remote Desktop Connection on Windows 10″… STOP it’s a bad idea and let me tell you why!
Months ago around November of 2021 it was late at night and I had one of those fun bad ideas. I decided to setup a honeypot at home on my personal gaming pc in a safe manner. What’s a honeypot? A honeypot is a computer or computer system that you connect to the internet and knowingly open it up to bad actors so they can compromise your computer. Basically login to your computer without your permission or hack it if you want to sound cool.

The idea is you dangle this piece of the pie aka your vulnerable computer in front of hackers so that they think there is something of value to them inside. Imagine a corporate network where the computers hold financial account numbers, social security numbers, or personal health information. The honeypot makes them think that’s what they may get if they break in but in reality you set up the trap just for them. You are silently waiting for them to attack and are ready to catch them in the act while recording their every move.
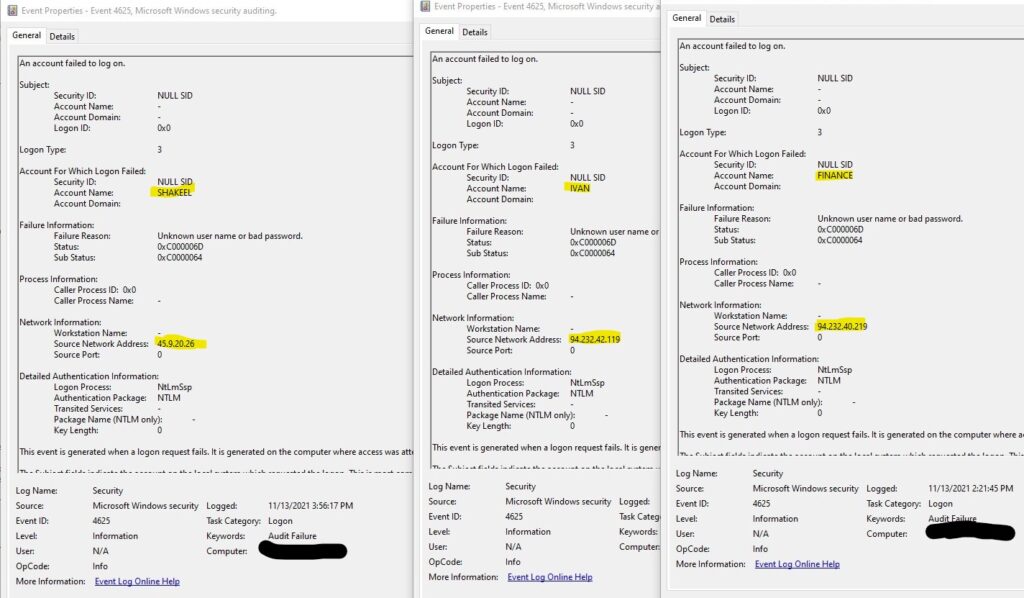
I really didn’t think this idea would pan out but I was wrong. Russian ip’s started hammering my gaming pc on November 13th of 2021 with a credential stuffing attack. I set up the trap within my Fortinet firewall with a new subnet. This new subnet was setup with an access policy that would only allow my gaming pc access to the internet and only one inbound connection to remote desktop services from the internet via port 1125. Segmentation was key!
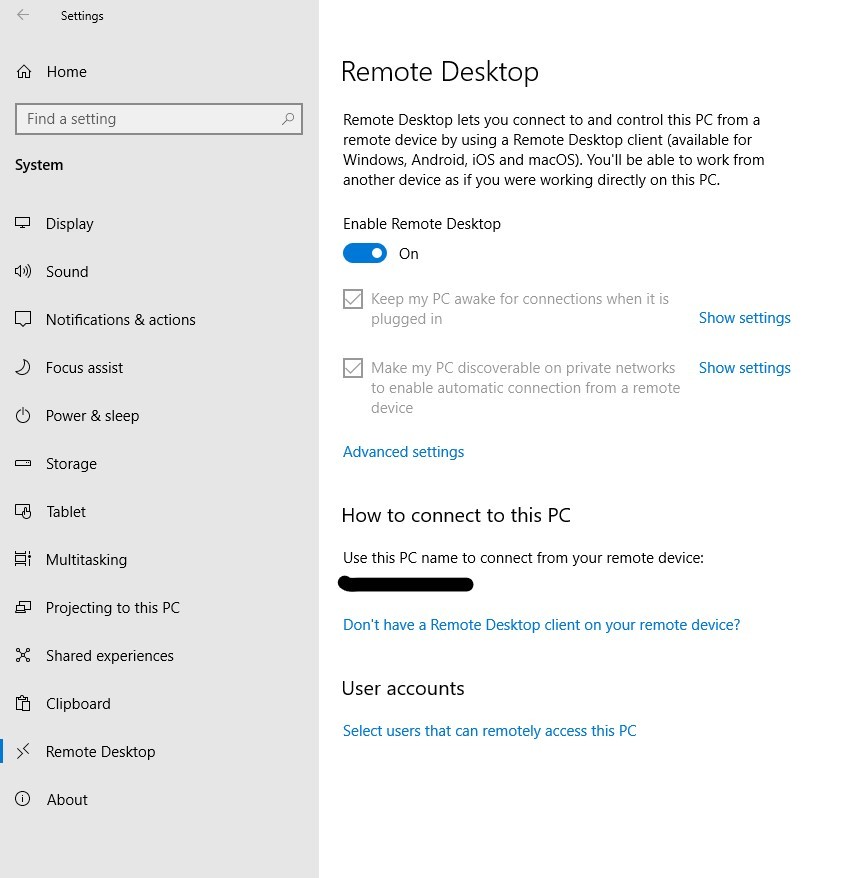
If you use windows you may have heard of Remote Desktop. This feature allows you to set up your personal computer at home to be logged into from a different computer at a different location. As seen in the screenshot above, all you have to do is toggle an on and off switch and you are ready to use remote desktop. With remote desktop on, you can type in your computers private ip address like 10.10.1.20:3389 and login to your computer. It’s that simple but also relatively safe if you don’t allow this feature to be accessed from the internet. Something those Youtube videos we spoke of earlier tell you to do.
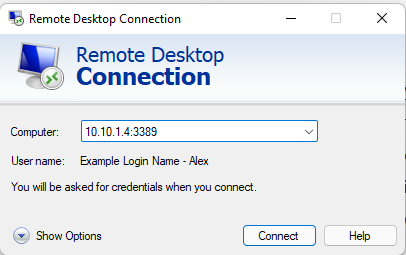
Above you see that I am using a program called Remote Desktop Connection, it’s how you connect to Remote Desktop Services. You will see the Remote Desktop Connection program ask for a computer name/ip address, the username of the person to login as, and then it would ask the password of the user. What is the number 3389? Port 3389 is the default port used by RDP that Microsoft set. Imagine your ip address is your homes address and a port number is the entrance sign that says “Bathroom” to your bathrooms door within your house. An example is if someone from the internet goes to your ip address and also points to port number 3389 it tells the computer “hey someone is trying to use this Microsoft RDP Service” or in this example your bathroom and let’s them proceed to try and get in or login in this case.
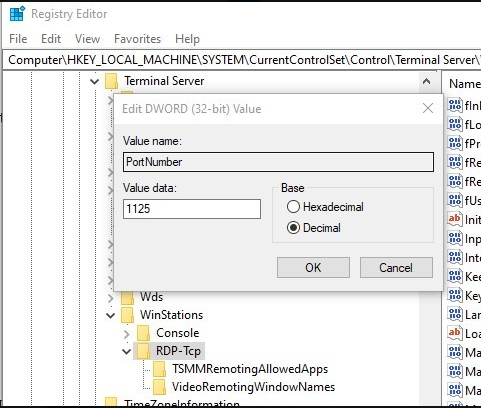
Now it’s not that simple to open up your computer and expose it to the internet. Just turning on Remote Desktop alone in Windows settings isn’t going to let you get hacked. You have to open up port 3389 in your home’s router to allow access from the internet into your computer. I won’t dig too deep into this part but in the screenshot above you see the numbers 1125. That was me changing Microsoft’s default port to remote desktop services from 3389 to 1125. Why did I do this? To bait a bad actor. I wanted someone to think why I wasn’t using the default Microsoft port for Remote Desktop Services 3389. Make the hacker think “maybe this person is saavy and of some importance”.
It worked. After some days of my computers Remote Desktop Services being exposed to the internet via port 1125, it got found. It started getting attacked by none other than… You got it. Russian ip addresses. The beauty of the internet is that there is always evidence of everything that has happened. You can delete files, delete logs, delete delete delete. There will always be artifacts and digital forensic evidence left of what was done on most technology devices with operations systems.
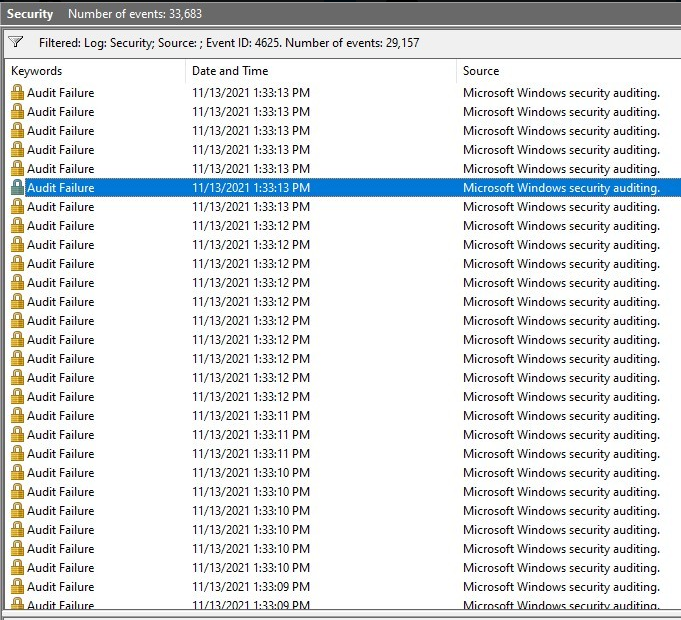
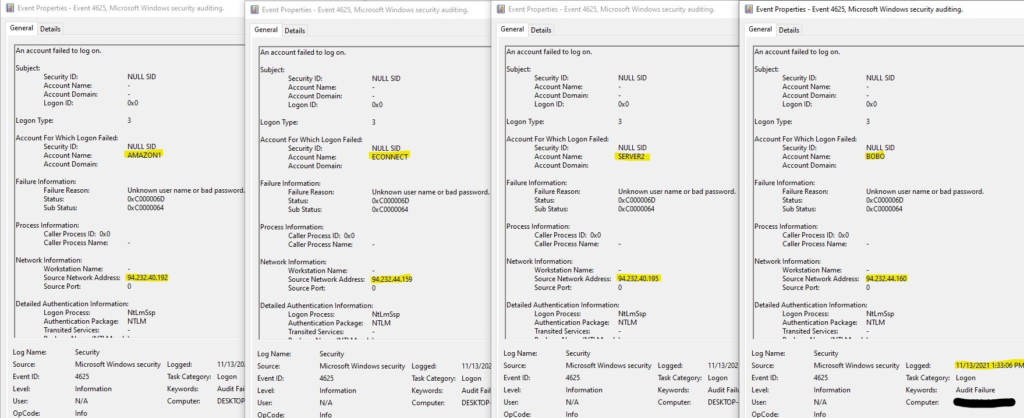
The bad actors Russian ip addresses kept pounding my gaming pc with around 8-15 login attempts per second and each of those login attempts has a different login name credential. This is what we call a credential stuffing attack where the hacker is using a database with well known leaked passwords and leaked usernames from past successful attacks. The login names ranged from Caisse, VisionOnline, Thao.NS, StacyB. Amazon1 and more.
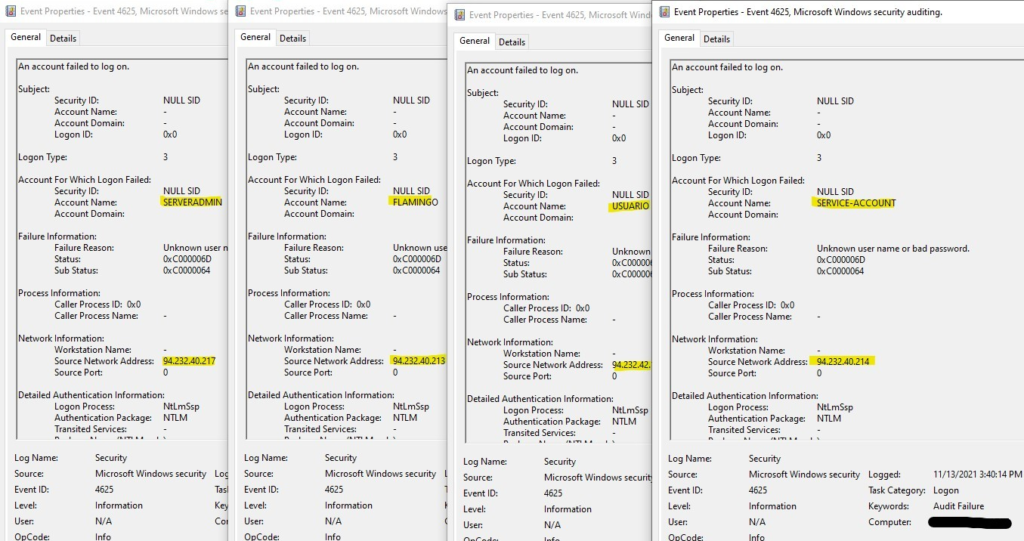
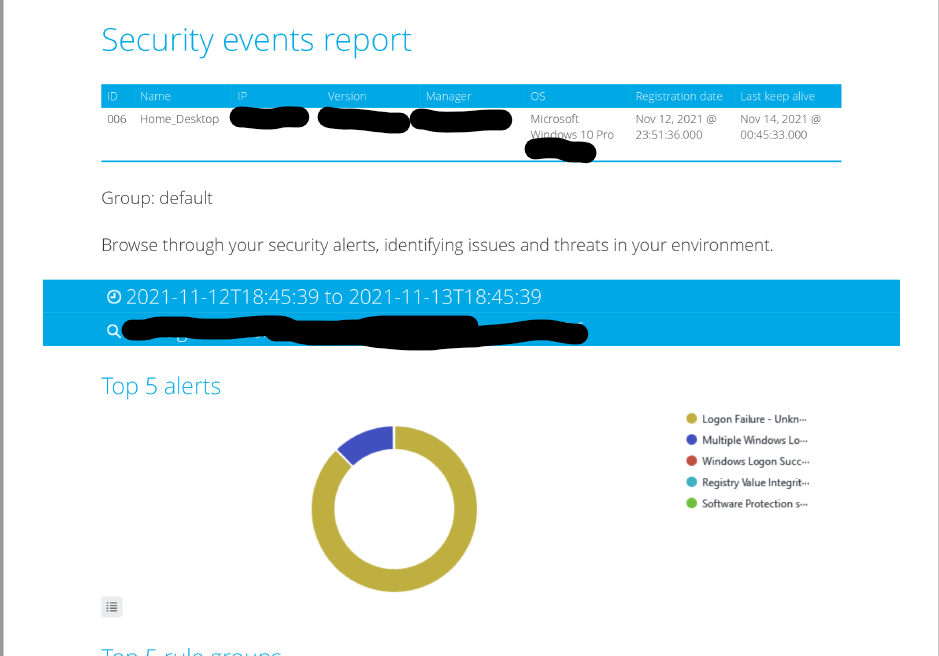
My SIEM virtual machine I setup for this project noticed the unusual behavior and notified me of these attempts to break into the system. I kept an eye on the attack until I gathered enough intelligence and began an incident response and remediation plan to get some practice in.
Moral of the story. The internet can be scary if you follow Youtube tutorials.